Cyber security is a complex topic a lot of non-technical people stay away from. One of the reasons for the aversion is it’s difficult to understand.
Don’t worry. We’ve got you covered.
If you’re not technically inclined, this article is for you. We covered 21 cyber security terms and provided real-world examples to help you understand them better.
21 Cyber Security Terms Every Business Owner Needs to Know
What is malware?
Malware comes from malicious software. It’s the generic term for viruses, worms, and other software designed to gain unauthorized access or cause damage to a computer. Think of it as whiskey and Scotch, or Champagne and sparkling wines. All Scotch are whiskey, but not all whiskey are Scotch.
What is ransomware?
Ransomware is a type of malware that prevents you from accessing your files until a ransom is paid. They do this by encrypting your files and asking for money. What that means is they add passwords to them. Since you don’t know the password and you obviously need to access your files, you’d be left with no choice but to pay the hacker.
What is two-factor authentication (2FA) or multi-factor authentication (MFA)?
2FA or MFA adds another layer of security to your accounts. That can be two (2FA) or more (MFA) depending on what you use. For example, before you can login your email, you need a password (first layer). If you have MFA enabled, it will also ask for a code (second layer) to be added. This code usually comes from an app or an SMS message. This means you need your phone with you (third layer).
What is the difference between two-factor authentication (2FA) or multi-factor authentication (MFA)?
Two Factor Authentication (2FA) is a form of Multi-Factor Authentication (MFA). The determining attribute here is that MFAs means two or more ways to protect your account.
What is the cloud?
The cloud is a technology that allows you to access our files and/or services through the internet from anywhere in the world. Technically speaking, it’s a collection of computers with large storage capabilities that remotely serve requests.
1. Malware

Malware is short for malicious software. It is any software designed to gain unauthorized access or to cause damage to a computer. It’s also the general (umbrella) term for all forms of malicious software.
Think of it as whiskey and Scotch, or Champagne and sparkling wines.
- All Scotch are whiskeys, but not all whiskeys are Scotch.
- All Champagne is sparkling wines, but not all sparkling wines are Champagne.
For it to be called Scotch or Champagne, they have to come from Scotland and Champagne, France directly.
It’s the same way for malware. These viruses and worms are all malware.
2. Ransomware
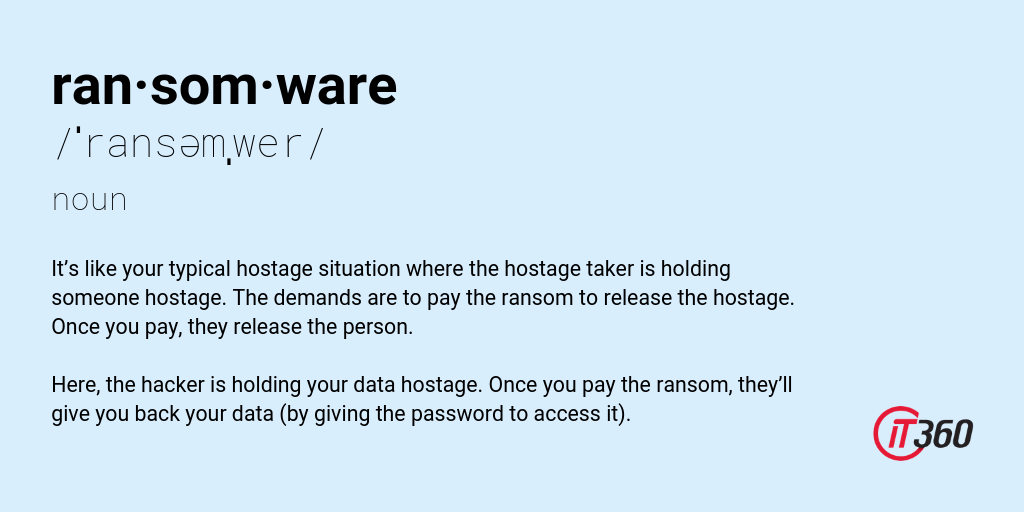
Ransomware is a type of malware that prevents you from accessing files on your computer until a ransom is paid. They do this by encrypting your files. What that means is they add passwords to it. Hacker then asks for money in exchange for the decryption key (password). Since you don’t know the password and you obviously need to access your files, you’d be left with no choice but to pay the hacker.
It’s like your typical hostage situation where the hostage taker is holding someone hostage. The demands are to pay the ransom to release the hostage. Once you pay, they release the person.
Here, the hacker is holding your data hostage. Once you pay the ransom, they’ll give you back your data (by giving the password to access it).
3. Social Engineering

Social engineering is a tactic that aims to convince a user to disclose sensitive information such as passwords and credit card numbers by impersonating other people. The most common social engineering example involves someone posing as the CEO and sends an email to the accounting/finance department to transfer money to a “supplier.”
For more information on this and how you can prevent your business from being targeted, download this free eBook on Who Are Your Organisation’s Top Targets?
4. Phishing

Phishing is the practice of sending fraudulent emails (or any other communication platform like SMS or calls) that resemble messages coming from reputable sources with the intention of stealing sensitive data like credit card numbers and login information.
Here’s an example of a phishing email where someone is pretending to be Apple. But if you look closely, you’d notice there are signs these are fake. For example, the email address contains a string of letters. Their domain is from akicintaopan.com, and not apple.com. And what might be the biggest factor, at least for me, is that Apple ID isn’t using this email address.
5. Vulnerability

A vulnerability is a weakness in design, implementation, operation or internal control. What this means is if one of the three pillars of cyber security is not addressed, your business is vulnerable.
You can think of vulnerabilities as weaknesses that you can take advantage of. For example, in football, you generally attack where there’s no defense present. If everyone is on the right side of the field, make a cross towards the left side and you have better chances of scoring a goal.
6. Denial-of-service (DoS)
DoS attacks are designed to make a computer or network resource unavailable to its intended users. This is usually done by one computer. There’s a version of this called Distributed Denial-of-Service (DDoS) which uses multiple computers to do the same thing.
Watch this quick video to show you what this might look like in real life. For more context, you can watch the entire clip.
7. Spoofing

Spoofing is the act of masquerading as a valid entity through falsification of data in order to gain access to information or resources that one is otherwise unauthorized to obtain.
This is similar to phishing in the sense that hackers try to deceive the person receiving it, but the main difference is that spoofing is for delivery whereas phishing is for retrieval.
You won’t knowingly download a malware, right? But if someone tricked you into clicking a link, say about your business getting sued, you will most likely click on it. That will then lead to a download of some sort of malware.
8. Adware
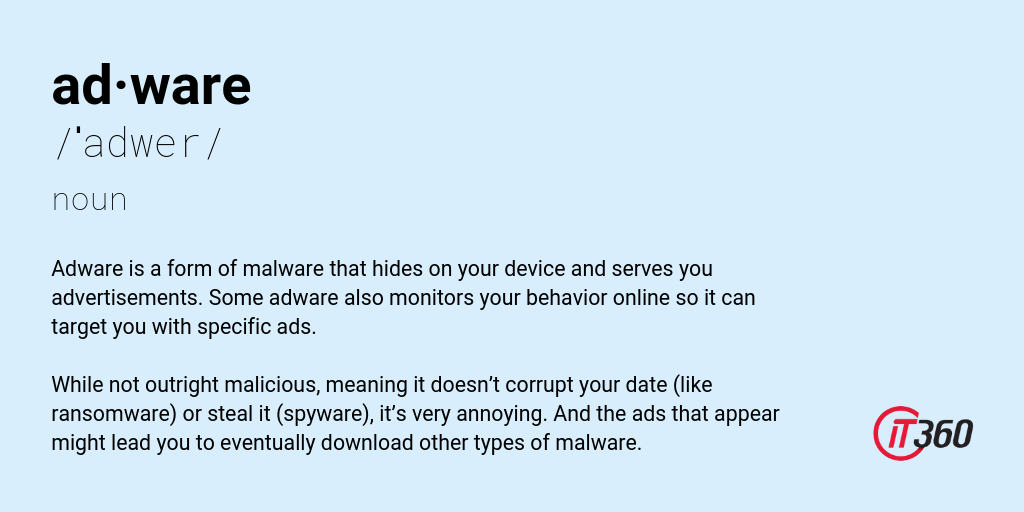
Adware is a form of malware that hides on your device and serves you advertisements. Some adware also monitors your behavior online so it can target you with specific ads.
Kaspersky recently wrote an article about a now-removed Chrome extension that started out as a regular plugin but became an adware — delivering unwanted ads every now and then.
While not outright malicious, meaning it doesn’t corrupt your date (like ransomware) or steal it (spyware), it’s very annoying. And the ads that appear might lead you to eventually download other types of malware.
9. Spyware

Spyware is a form of malware that hides on your device, monitors your activity, and steals sensitive information like bank details and passwords.
You can think of this as “Big Brother” but in a bad way. Everything you do — what you watch and what you type — gets monitored. If you login your bank and didn’t have multi-factor authentication, someone can easily access your money.
10. Trojan

Trojans are programs that claim to perform one function but actually do another, typically malicious. Trojans can take the form of attachments, downloads, and fake videos/programs.
While there are many types of trojans, the concept is simple. Hackers try to get in your computers by promising to do something (fake program), but later does something else (give them access to your system).
Remember the story of Troy and how the Greeks lay ruin to the walled city?
After years of war, the Greeks created the Trojan Horse, sailed away, and left one man behind. This man convinced the people of Troy that they abandoned him and left the horse as an offering to the goddess Athena. The Trojans pulled the horse back into Troy. Later that night, a small Greek army emerged from inside the horse and opened the gates for the rest of the Greek army (which sailed back under during the night) to enter; thus, destroying the city of Troy and ending the war.
11. Keylogger
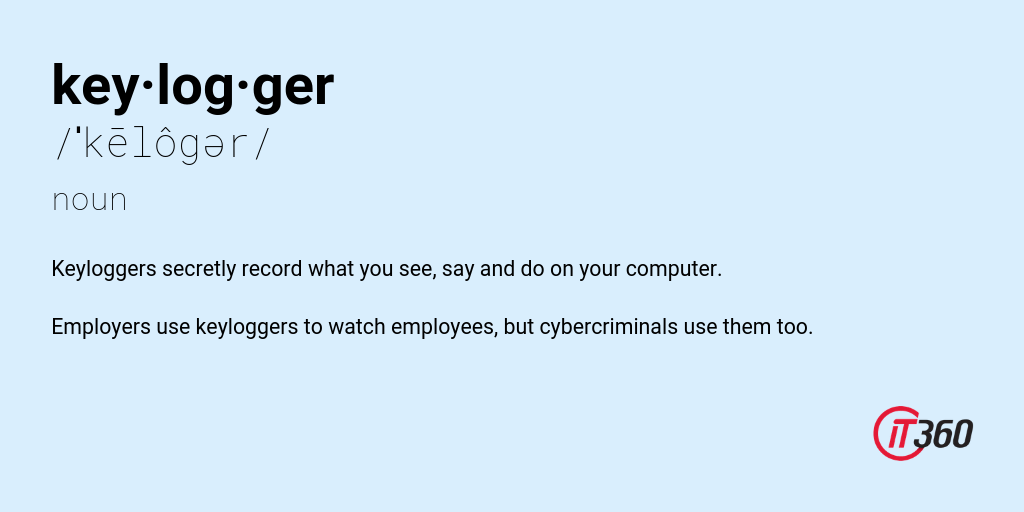
Keyloggers secretly record what you see, say and do on your computer. Employers use keyloggers to watch employees, but cybercriminals use them too.
Keyloggers lies on the border of a productivity tool and a spyware. The main difference is where the data is used. Take, for example, this employee who sued his employer for illegal dismissal.
12. Two-Factor Authentication / Multi-Factor Authentication
Two Factor Authentication (2FA) is a form of Multi-Factor Authentication (MFA). The determining attribute here is that MFAs mean two or more ways to protect your account.
Do you use an ATM to access your cash? If you do, then you’re already using a form of multi-factor authentication.
In order to withdraw your cash, you would need the following:
- Your ATM card
- Your PIN
That’s an added layer of security banks (and other services you use) to protect you. If you lost your wallet, someone can easily withdraw from your account if you don’t have a PIN.
13. Cloud
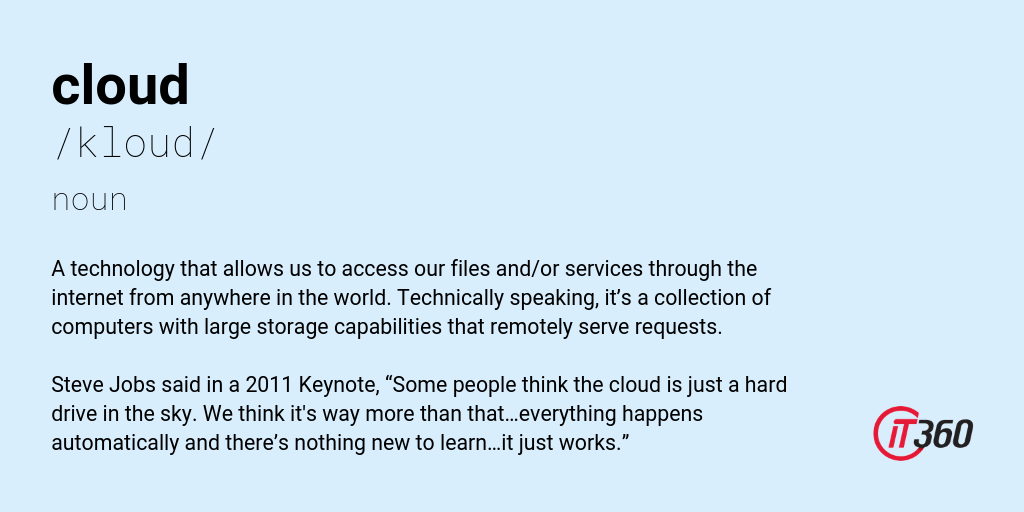
A technology that allows us to access our files and/or services through the internet from anywhere in the world. Technically speaking, it’s a collection of computers with large storage capabilities that remotely serve requests.
Steve Jobs said in a 2011 Keynote, “Some people think the cloud is just a hard drive in the sky. We think it’s way more than that…everything happens automatically and there’s nothing new to learn…it just works.”
You can watch the video below…
While he talked about their product, iCloud, the cloud works in the same way. It works in the background to help you do what you need to do.
14. Software
A set of programs that tell a computer to perform a task. These instructions are compiled into a package that users can install and use. For example, Microsoft Office is an application software.
A simple way to think of software is it’s what you interact with on your devices. The apps on your phone are all software. The programs you are using on your laptops and computers are software.
15. Virtual Private Network (VPN)
A virtual private network (VPN) is a tool that allows you to remain anonymous while using the internet. It does this by masking your location and encrypting your traffic.
Take a look at this image…
When you connect to the internet, it goes through a series of steps that happens behind the scenes.
- From your device, it goes to a router (whether public or private)
- From that router, it heads to your internet service provider (ISP)
- From your ISP, it reaches the internet
As the image depicts, with VPN, the data gets encrypted the moment it leaves your device. No one can snoop around wherever they are.
16. Encryption
Encryption, in its simplest form, is to add a password to your data so that anyone who doesn’t know the password (called the decryption key), can’t view it. This doesn’t mean that the encrypted data can’t be stolen, though.
One example of this is adding a passcode to your phone. Without that passcode, your phone (and all data in it) is encrypted. Even if your phone is stolen, without them knowing that code, they won’t be able to access the contents.
17. Data Breach
A data breach is the moment information is accessed without authorization. This includes both external and internal actors (yes, these are employees).
For example, the biggest data breach that welcomed the 2019 is called Collection #1, where over 1.2 billion unique combination of email addresses and passwords were leaked to the public.
18. Firewall
A firewall is a hardware or software designed to filter traffic coming in and out of your network or computer. That filter is based on a set of security rules.
You can think of the firewall as similar to the immigration services. People coming in/out of the country passes through a set of protocols. They can’t just allow people to come in without visas or going through a certain process.
19. IP Address
An IP address, short for internet protocol address, is an internet version of a home address for your computer, which is identified when it communicates over a network.
There are two versions of IP addresses used today: IPv4 and IPv6. Here are examples for each version, respectively: 172.16.254.1 and 2001:db8:0:1234:0:567:8:1.
Again, you can think of this as your home address. Your address allows people to go to your home. Or, it allows maps to determine your location and come up with the best driving route.
This is why a VPN is important because without it, you and your location will be sent to anyone who knows your IP address.
20. Virus
A virus is a type of malware aimed to corrupt, erase or modify information on a computer before spreading to others.
See also worm below
21. Worm
A worm is piece of malware that can replicate itself in order to spread the infection to other connected computers. It’s also a type of a virus.
Viruses and worms both have the ability to propagate and spread to other devices. The main difference between them is that a virus needs a a program (e.g. a word document) to cause damage whereas a worm doesn’t.
Do you remember the Friends episode where Chandler borrows Ross’ laptop to check his email? After clicking on the ‘photo’ that was sent by someone he didn’t know, it erased the laptop’s entire hard drive. That’s an example of a worm.
Conclusion
There are a lot more cyber security terms out there. Some organizations even have their own A to Z dictionary of these. Here, we only listed the most common terms you will moist likely encounter.
Did the analogies help you understand them better? Did we miss anything? Let us know in the comments below.



2 thoughts on “21 Cyber Security Terms Business Owners Need to Know (Including Analogies to Help You Understand Them Better)”